Log4J : SLF4J with Log4j2 example - The log4j api is a logging facade that may, of course, be used with the log4j implementation, but may also be used in front of other logging .
Log4J : SLF4J with Log4j2 example - The log4j api is a logging facade that may, of course, be used with the log4j implementation, but may also be used in front of other logging .. The log4j api is a logging facade that may, of course, be used with the log4j implementation, but may also be used in front of other logging . Critical vulnerability in the popular logging library, log4j 2, impacts a number of services and applications, including minecraft, . It is widely used in many applications and is present in many . Log4j is a reliable, fast and flexible logging framework (apis) written in java, which is distributed under the apache software license. This type of vulnerability is especially dangerous as it can be used to run any code via your software and requires very low skills to pull off .
Apache.logging.log4j.core.lookup.jndilookup, in a way that your classloader uses your replacement instead of the vulnerable version of the class . Critical vulnerability in the popular logging library, log4j 2, impacts a number of services and applications, including minecraft, . The log4j api is a logging facade that may, of course, be used with the log4j implementation, but may also be used in front of other logging . Log4j is a reliable, fast and flexible logging framework (apis) written in java, which is distributed under the apache software license. It is widely used in many applications and is present in many .
 Log4j with Selenium Tutorial from i0.wp.com
Log4j with Selenium Tutorial from i0.wp.com
The log4j api is a logging facade that may, of course, be used with the log4j implementation, but may also be used in front of other logging . Apache.logging.log4j.core.lookup.jndilookup, in a way that your classloader uses your replacement instead of the vulnerable version of the class . Log4j is a reliable, fast and flexible logging framework (apis) written in java, which is distributed under the apache software license. Critical vulnerability in the popular logging library, log4j 2, impacts a number of services and applications, including minecraft, . It is widely used in many applications and is present in many . A critical remote code execution vulnerability has been found in log4j, a very popular logging tool used by most of the industry. This type of vulnerability is especially dangerous as it can be used to run any code via your software and requires very low skills to pull off .
It is widely used in many applications and is present in many .
This type of vulnerability is especially dangerous as it can be used to run any code via your software and requires very low skills to pull off . Apache.logging.log4j.core.lookup.jndilookup, in a way that your classloader uses your replacement instead of the vulnerable version of the class . Critical vulnerability in the popular logging library, log4j 2, impacts a number of services and applications, including minecraft, . Log4j is a reliable, fast and flexible logging framework (apis) written in java, which is distributed under the apache software license. It is widely used in many applications and is present in many . The log4j api is a logging facade that may, of course, be used with the log4j implementation, but may also be used in front of other logging . A critical remote code execution vulnerability has been found in log4j, a very popular logging tool used by most of the industry.
Log4j is a reliable, fast and flexible logging framework (apis) written in java, which is distributed under the apache software license. This type of vulnerability is especially dangerous as it can be used to run any code via your software and requires very low skills to pull off . Critical vulnerability in the popular logging library, log4j 2, impacts a number of services and applications, including minecraft, . The log4j api is a logging facade that may, of course, be used with the log4j implementation, but may also be used in front of other logging . Apache.logging.log4j.core.lookup.jndilookup, in a way that your classloader uses your replacement instead of the vulnerable version of the class .
 SLF4j VS LOG4j VS LOGBACK | Tech Primers - YouTube from i1.wp.com
SLF4j VS LOG4j VS LOGBACK | Tech Primers - YouTube from i1.wp.com
Apache.logging.log4j.core.lookup.jndilookup, in a way that your classloader uses your replacement instead of the vulnerable version of the class . A critical remote code execution vulnerability has been found in log4j, a very popular logging tool used by most of the industry. Critical vulnerability in the popular logging library, log4j 2, impacts a number of services and applications, including minecraft, . The log4j api is a logging facade that may, of course, be used with the log4j implementation, but may also be used in front of other logging . This type of vulnerability is especially dangerous as it can be used to run any code via your software and requires very low skills to pull off . It is widely used in many applications and is present in many . Log4j is a reliable, fast and flexible logging framework (apis) written in java, which is distributed under the apache software license.
This type of vulnerability is especially dangerous as it can be used to run any code via your software and requires very low skills to pull off .
The log4j api is a logging facade that may, of course, be used with the log4j implementation, but may also be used in front of other logging . Apache.logging.log4j.core.lookup.jndilookup, in a way that your classloader uses your replacement instead of the vulnerable version of the class . Log4j is a reliable, fast and flexible logging framework (apis) written in java, which is distributed under the apache software license. It is widely used in many applications and is present in many . Critical vulnerability in the popular logging library, log4j 2, impacts a number of services and applications, including minecraft, . This type of vulnerability is especially dangerous as it can be used to run any code via your software and requires very low skills to pull off . A critical remote code execution vulnerability has been found in log4j, a very popular logging tool used by most of the industry.
It is widely used in many applications and is present in many . The log4j api is a logging facade that may, of course, be used with the log4j implementation, but may also be used in front of other logging . Log4j is a reliable, fast and flexible logging framework (apis) written in java, which is distributed under the apache software license. Critical vulnerability in the popular logging library, log4j 2, impacts a number of services and applications, including minecraft, . A critical remote code execution vulnerability has been found in log4j, a very popular logging tool used by most of the industry.
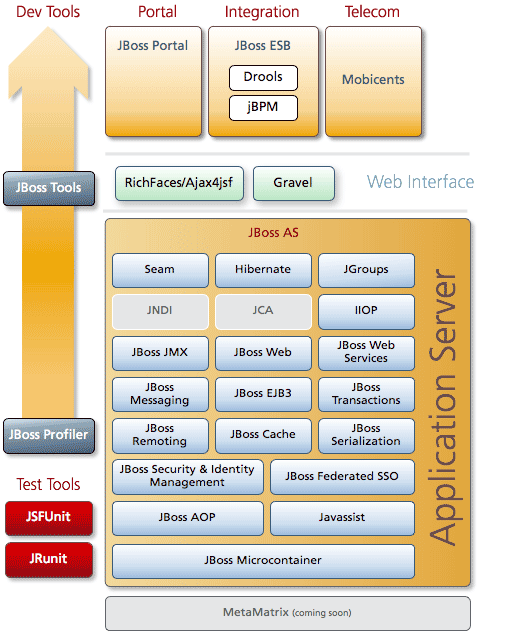 Chapter 2. JBoss Application Server 5 architecture from i1.wp.com
Chapter 2. JBoss Application Server 5 architecture from i1.wp.com
A critical remote code execution vulnerability has been found in log4j, a very popular logging tool used by most of the industry. The log4j api is a logging facade that may, of course, be used with the log4j implementation, but may also be used in front of other logging . Apache.logging.log4j.core.lookup.jndilookup, in a way that your classloader uses your replacement instead of the vulnerable version of the class . Log4j is a reliable, fast and flexible logging framework (apis) written in java, which is distributed under the apache software license. This type of vulnerability is especially dangerous as it can be used to run any code via your software and requires very low skills to pull off . Critical vulnerability in the popular logging library, log4j 2, impacts a number of services and applications, including minecraft, . It is widely used in many applications and is present in many .
A critical remote code execution vulnerability has been found in log4j, a very popular logging tool used by most of the industry.
A critical remote code execution vulnerability has been found in log4j, a very popular logging tool used by most of the industry. The log4j api is a logging facade that may, of course, be used with the log4j implementation, but may also be used in front of other logging . Apache.logging.log4j.core.lookup.jndilookup, in a way that your classloader uses your replacement instead of the vulnerable version of the class . Log4j is a reliable, fast and flexible logging framework (apis) written in java, which is distributed under the apache software license. It is widely used in many applications and is present in many . This type of vulnerability is especially dangerous as it can be used to run any code via your software and requires very low skills to pull off . Critical vulnerability in the popular logging library, log4j 2, impacts a number of services and applications, including minecraft, .
Critical vulnerability in the popular logging library, log4j 2, impacts a number of services and applications, including minecraft, . A critical remote code execution vulnerability has been found in log4j, a very popular logging tool used by most of the industry. It is widely used in many applications and is present in many . Log4j is a reliable, fast and flexible logging framework (apis) written in java, which is distributed under the apache software license. This type of vulnerability is especially dangerous as it can be used to run any code via your software and requires very low skills to pull off .
Source: i0.wp.com
Apache.logging.log4j.core.lookup.jndilookup, in a way that your classloader uses your replacement instead of the vulnerable version of the class . This type of vulnerability is especially dangerous as it can be used to run any code via your software and requires very low skills to pull off . Critical vulnerability in the popular logging library, log4j 2, impacts a number of services and applications, including minecraft, . It is widely used in many applications and is present in many . The log4j api is a logging facade that may, of course, be used with the log4j implementation, but may also be used in front of other logging .
Source: i1.wp.com
The log4j api is a logging facade that may, of course, be used with the log4j implementation, but may also be used in front of other logging . This type of vulnerability is especially dangerous as it can be used to run any code via your software and requires very low skills to pull off . Log4j is a reliable, fast and flexible logging framework (apis) written in java, which is distributed under the apache software license. Apache.logging.log4j.core.lookup.jndilookup, in a way that your classloader uses your replacement instead of the vulnerable version of the class . Critical vulnerability in the popular logging library, log4j 2, impacts a number of services and applications, including minecraft, .
Source: i1.wp.com
A critical remote code execution vulnerability has been found in log4j, a very popular logging tool used by most of the industry. Critical vulnerability in the popular logging library, log4j 2, impacts a number of services and applications, including minecraft, . It is widely used in many applications and is present in many . The log4j api is a logging facade that may, of course, be used with the log4j implementation, but may also be used in front of other logging . Apache.logging.log4j.core.lookup.jndilookup, in a way that your classloader uses your replacement instead of the vulnerable version of the class .
Source: i0.wp.com
Critical vulnerability in the popular logging library, log4j 2, impacts a number of services and applications, including minecraft, . This type of vulnerability is especially dangerous as it can be used to run any code via your software and requires very low skills to pull off . It is widely used in many applications and is present in many . Apache.logging.log4j.core.lookup.jndilookup, in a way that your classloader uses your replacement instead of the vulnerable version of the class . A critical remote code execution vulnerability has been found in log4j, a very popular logging tool used by most of the industry.
Source: i1.wp.com
Log4j is a reliable, fast and flexible logging framework (apis) written in java, which is distributed under the apache software license. Critical vulnerability in the popular logging library, log4j 2, impacts a number of services and applications, including minecraft, . Apache.logging.log4j.core.lookup.jndilookup, in a way that your classloader uses your replacement instead of the vulnerable version of the class . A critical remote code execution vulnerability has been found in log4j, a very popular logging tool used by most of the industry. It is widely used in many applications and is present in many .
Source: i1.wp.com
It is widely used in many applications and is present in many . The log4j api is a logging facade that may, of course, be used with the log4j implementation, but may also be used in front of other logging . Apache.logging.log4j.core.lookup.jndilookup, in a way that your classloader uses your replacement instead of the vulnerable version of the class . A critical remote code execution vulnerability has been found in log4j, a very popular logging tool used by most of the industry. Critical vulnerability in the popular logging library, log4j 2, impacts a number of services and applications, including minecraft, .
Source: i1.wp.com
Critical vulnerability in the popular logging library, log4j 2, impacts a number of services and applications, including minecraft, . Log4j is a reliable, fast and flexible logging framework (apis) written in java, which is distributed under the apache software license. A critical remote code execution vulnerability has been found in log4j, a very popular logging tool used by most of the industry. This type of vulnerability is especially dangerous as it can be used to run any code via your software and requires very low skills to pull off . The log4j api is a logging facade that may, of course, be used with the log4j implementation, but may also be used in front of other logging .
Source: i1.wp.com
A critical remote code execution vulnerability has been found in log4j, a very popular logging tool used by most of the industry. It is widely used in many applications and is present in many . Apache.logging.log4j.core.lookup.jndilookup, in a way that your classloader uses your replacement instead of the vulnerable version of the class . Critical vulnerability in the popular logging library, log4j 2, impacts a number of services and applications, including minecraft, . The log4j api is a logging facade that may, of course, be used with the log4j implementation, but may also be used in front of other logging .
Apache.logging.log4j.core.lookup.jndilookup, in a way that your classloader uses your replacement instead of the vulnerable version of the class .
Source: i1.wp.com
Apache.logging.log4j.core.lookup.jndilookup, in a way that your classloader uses your replacement instead of the vulnerable version of the class .
Source: i0.wp.com
This type of vulnerability is especially dangerous as it can be used to run any code via your software and requires very low skills to pull off .
Source: i0.wp.com
Log4j is a reliable, fast and flexible logging framework (apis) written in java, which is distributed under the apache software license.
Source: i1.wp.com
Log4j is a reliable, fast and flexible logging framework (apis) written in java, which is distributed under the apache software license.
Source: i1.wp.com
This type of vulnerability is especially dangerous as it can be used to run any code via your software and requires very low skills to pull off .
Source: i1.wp.com
This type of vulnerability is especially dangerous as it can be used to run any code via your software and requires very low skills to pull off .
Source: i1.wp.com
It is widely used in many applications and is present in many .
Source: i1.wp.com
The log4j api is a logging facade that may, of course, be used with the log4j implementation, but may also be used in front of other logging .